The release includes the introduction of API Keys for authentication, the ability to add custom tables to documents, and improvements to various functions such as scheduling validation and data replication. Several bugs were also fixed, including issues related to printing, filtering, and linking AFEs to WellEz jobs.
Schema Changes
- Added new APIKEY* tables to store API Keys.
- Added “CREATOR” columns to RTX, RTD, RTX_H and RTD_H tables.
Features️
-
Introduced API Keys, a better and more secure way of authenticating to Execute when building integrations against the Execute APIs. For those of you with existing API-based integrations, it is probably worthwhile migrating away from username/password and toward our API keys when possible.
#integration
#165516
We’ve added the ability to create API Keys to Execute to make it easier/safer to write integrations against the Execute APIs.
- By default, only admins can create a new API key.
- Sessions created using an API Key do not consume or require a license.
- API Keys can be set to expire (user-created API Keys must expire within one year).
- API Keys work much better in an environment that doesn’t have passwords (i.e., SSO users).
The Problem
Execute has a great set of APIs that many of you use to build integrations between Execute and other systems. Unfortunately, to use these Execute APIs, you needed to create a session using a username and password and the normal login API (used by the app itself). This raises several problems:
- It Doesn’t work well for environments that use SSO and don’t have passwords.
- Execute’s normal sessions consume/require a license. This requirement means that integrations start failing when the system is busy because they can’t get a license. It also means that for clients with small numbers of licenses, a long-running integration may lock people out of the system.
- Execute’s default 2-minute timeout on a session can break long-running integrations.
What is an API Key?
In Execute, an API key is an additional credential that can be used to log into the Execute APIs (or OData) to facilitate integrations. It’s like an additional username and password that are machine-generated (long and secure). Creating a session using an API Key does not consume a license and is more robust than the old-style login.
Creating an API Key
API Keys are managed under
Tools > Configuration > API Keys.It is always a best practice to create unique API Keys for each service/integration to simplify phasing out old credentials or replacing compromised ones.
Admin API Keys
Users with the new
Manage API Keysprivilege are always able to add new API Keys using theCreate API Keybutton on the top of the API Keys screen.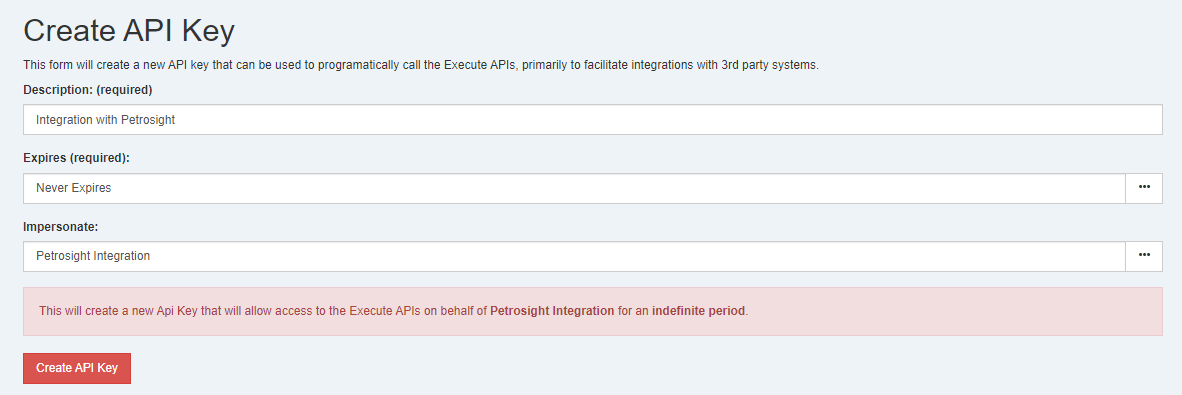
- A description is always required for an API key and should describe what the key is being used for. A good description might be something like “Integration with Petrosight” or “Data Warehouse”
- You must define when the key expires. Administrators can create API Keys that never expire.
- An admin may also configure the key to impersonate another user. Doing so means that all APIs called using the new API Key will operate as if the impersonated user was calling them. Impersonation is commonly required so an admin can set up an API key for a service account in Execute that they can’t log into directly.
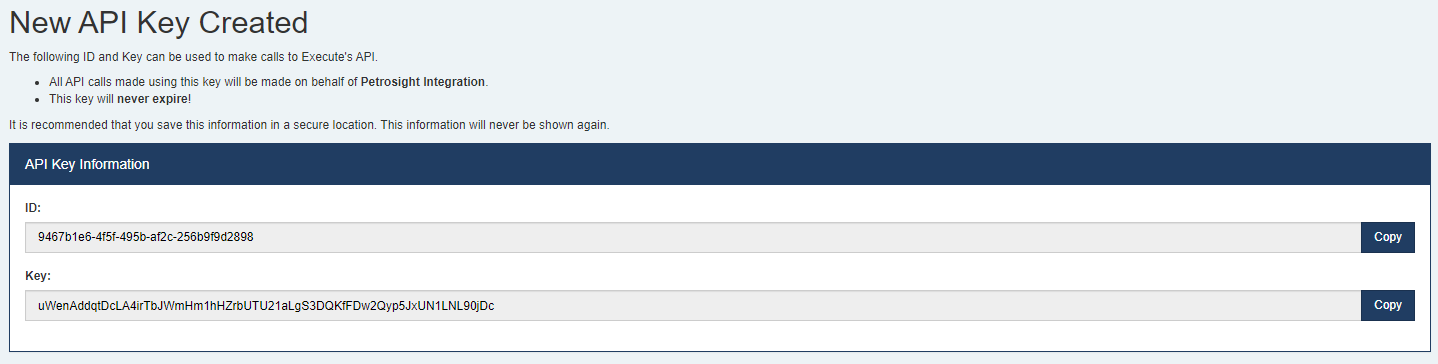
Once created, you need to note the
IDand theKeyas both are required to use the APIs. TheKeywill never be shown again. TheIDis just the DocumentID for the newly createdAPI Keydocument and is not a secret.Non-admin API Keys
By default, non-admin users can NOT create new API Keys. You can permit users to create API Keys by toggling the new
Allow non-admin users to create API Keys?setting to “Yes”.The typical use-case for non-admin self-serve API keys is to support OData use in password-less environments. Alternatively, if only a few users need API Keys, administrators can create API Keys that impersonate that user, and then securely share the
IdandKeywith the user.When permitted, users can create a new API Key (for themselves) using the
Create API Keybutton at the top of the API Keys screen.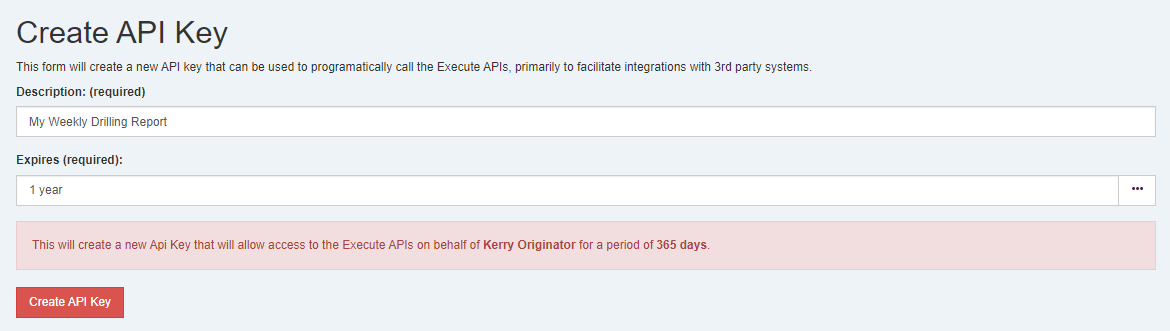
- A description is always required for an API key and should describe what the key is being used for. A good description might be something like “OData Summary Report” or “Data Warehouse”
- You must define when the key expires. Non-admin users can set a maximum expiry of 1 year.
- Non-admin users can NEVER create API Keys that impersonate other users.
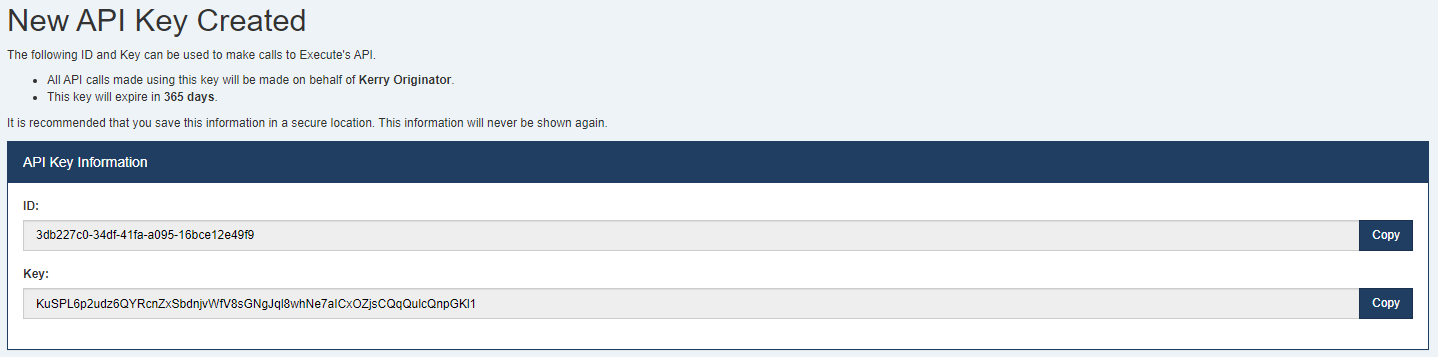
As before, once created, you need to note the
IDand theKeyas both are required to use the APIs. TheKeywill never be shown again. TheIDis just the DocumentID for the newly createdAPI Keydocument and is not a secret.Viewing and Editing API Keys
Current API Keys can be viewed from
Tools > Configuration > API Keys.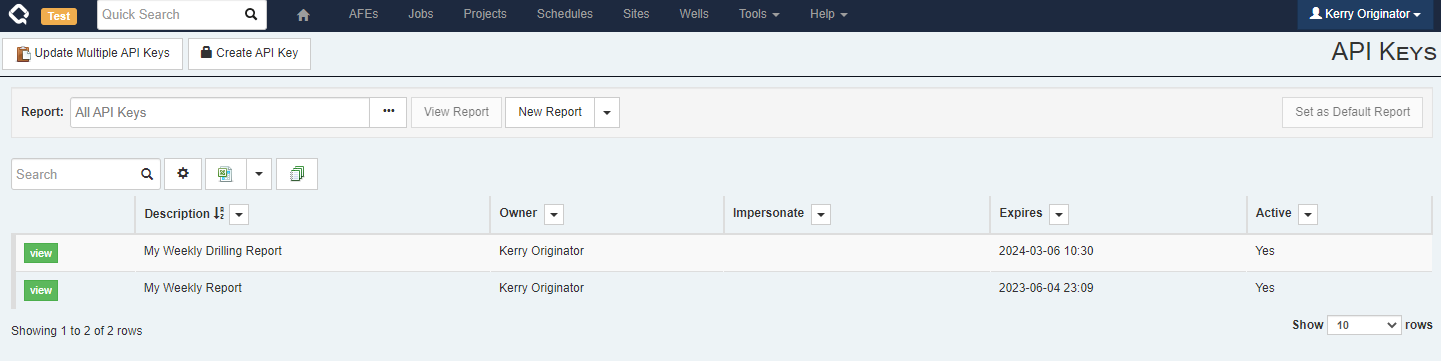
- Administrative users with
Manage API Keyswill see all API Keys across all users in the system - Non-admin users will only see API Keys that they created and those created by other users that impersonate them
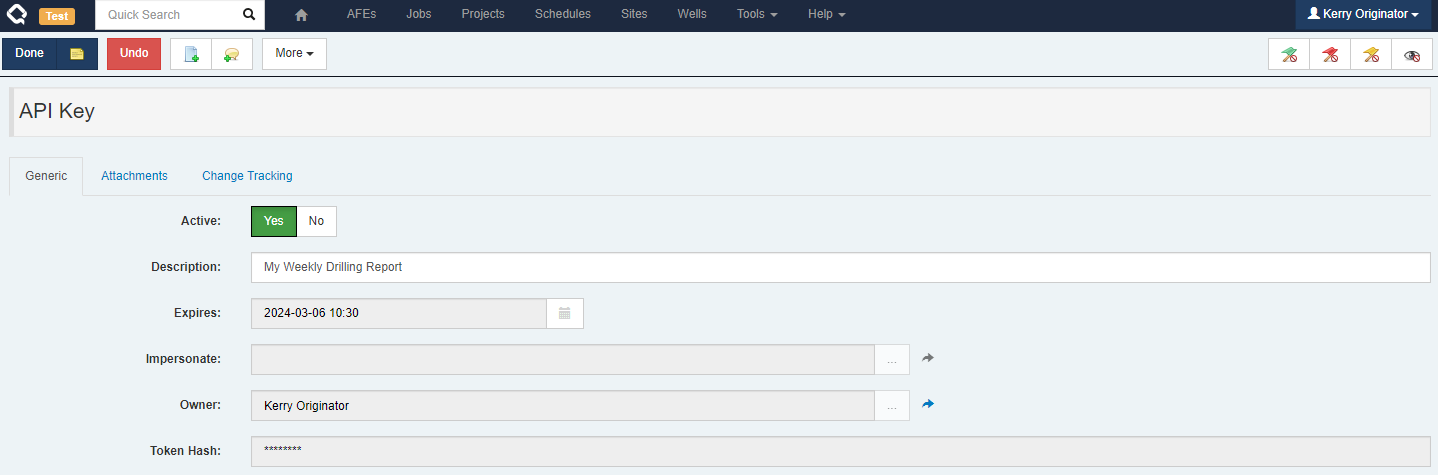
Either the owner of an API Key or an admin can change an API Key, but those changes are limited to:
- Toggle the “Active” flag on an API Key (temporarily enable/disable it)
- Deleting the API Key
- Updating the API Key description
Once an API Key is created, there is no way to change the user to impersonate or the expiry time.
Managing API Sessions
When an API Key is in use, administrators will see it under the
Manage Sessionsscreen, where they can terminate it if required.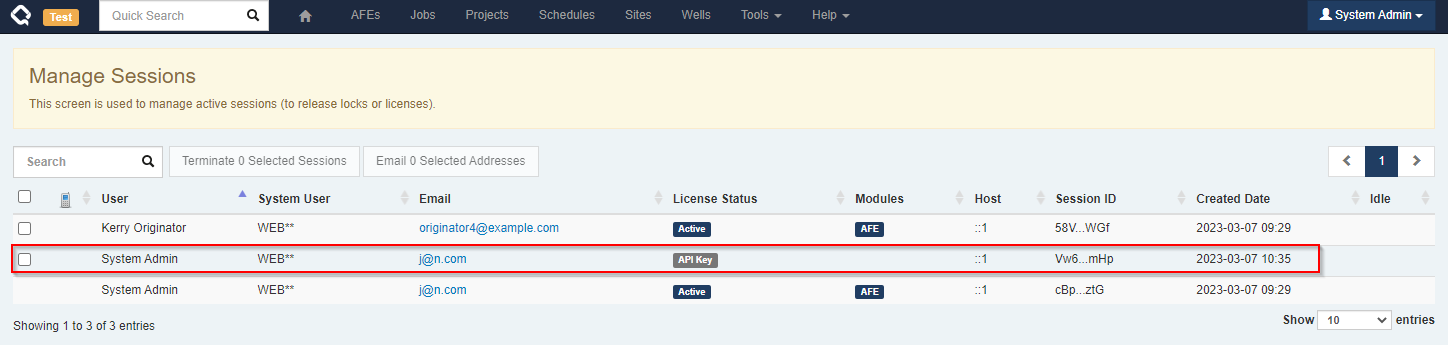
API Sessions are different
- Only a single active session is permitted for an API key (whereas you can log in multiple times with a username/password)
- API Key sessions timeout after an hour instead of the usual 2 minutes
- API Key sessions do not consume a license
Because of the above, the primary reason to terminate an API Session is if it was accidentally left open and you’d like to terminate it so a new session can be created and any locks it holds can be released.
Using an API Key with Execute
API Keys can be used to call Execute’s APIs, and can also be used for OData.
APIs
Calling any Execute APIs requires you have a valid session.
To create a new Execute session using an API key, call the new
/api/Authentication/ApiKey/LoginAPI instead of the previous/api/Authentication/LoginAPI.The arguments to this API are simply the ID and Key obtained when creating the API Key.
{ "Id": "a426fcff-6569-4aa6-a596-4dba1469c425", "Key": "SK9EwPMwMX4CYKMX6Xc7JMchJp5ZyWEUdAIni5V3OwS6nLfAHZJHrKd8vnruIBnD" }The response from the ApiKey/Login call is identical to the normal login call. If the API Key impersonates a user the session will be created as that user.
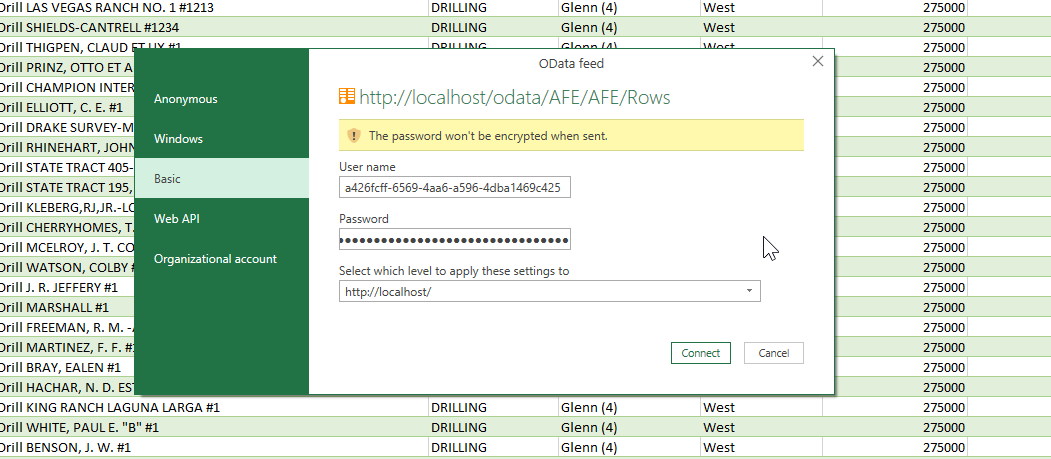
OData
The new API Keys can also be used to connect to OData for environments/situations where the normal username and password is not appropriate.
-
Execute now allows you to add additional custom tables to your documents to allow you to better lay out custom fields, as well as handle very large numbers of fields (more than 1000). For those of you implementing many new workflows in RTx and watching your custom field count climb steadily upward, you can breath easier now.
#system
#175816
When you add custom fields to Execute, they are typically added to a single
_CUSTOMtable. It turns out that there is a maximum number of columns supported in a table (it varies by database configuration) but it’s roughly around 1000. This can be a problem for organization implementing many RTx-type workflows.To alleviate this, you can now add additional storage tables in Execute from a document’s configuration page.
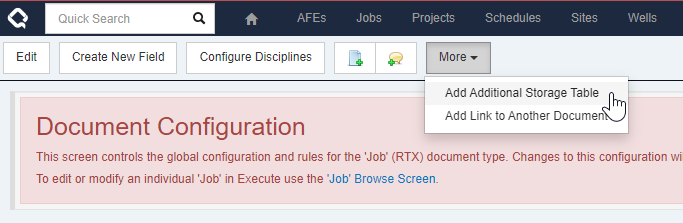
In this example, we’re adding a new storage table for fields related to our abandonment process. We could also just call it Custom 2 if we don’t want to separate fields by type.
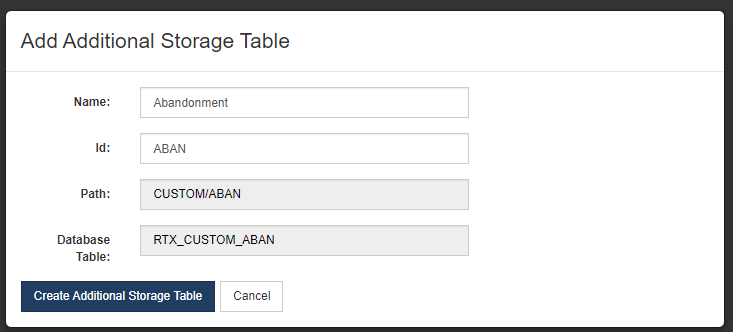
Once created, new fields can be added to the new table by selecting it as the “Record” when adding a new field.
Enhancements
- We’ve updated the version of NSIS (the software that powers the Execute installer) and, while we were at it, we now display the version of Execute being installed in the installer to help avoid any “oops, I installed the wrong version” type mishaps. #system #230486
- The creator of a document link, and an administrator, are now able to update the comment on document links without removing and recreating the link. Helpful for fixing up those embarrassing typos. #ui #231482
- We added a new warning when exporting from OpSched to Enersight to highlight any step groups that are partially scheduled. Enersight requires that all activities in a step group are either scheduled or unscheduled, and this helps catch those cases where that condition isn’t met. #opsched #enersight #231963
- If you were curious about who created that RTD/RTx/Job vs. who owns it now, we’ve added a new “Creator” column and backfilled it for all of your historical data using Execute’s version history. #well delivery #233601
- Improved the error message when the Integration Agent Data Replicator failed due to a column-type mismatch. The error now shows the offending data types. #integration agent #233688
- Added a new schedule validation that highlights activities in a step group with inconsistent use of the “Scheduled” flag. For activities in a step group, it is required/expected that they all be scheduled, or all be unscheduled. #opsched #234126
-
Added some nice navigation arrows to make it easier to open the related root document for a workflow task from the dashboard widgets, and the task completion popup.
#workflow
#235278
If you are using Execute’s Advanced (Task-based) Workflows, to help guide the workflow for an AFE or a Job, it turns out it wasn’t easy to find your way back to the underlying AFE/Job if you wanted to see the whole picture.
In this update, we’ve added helpful little icons in the “My Active Tasks” and “Group Active Tasks” widgets that will bring you directly to the root document.
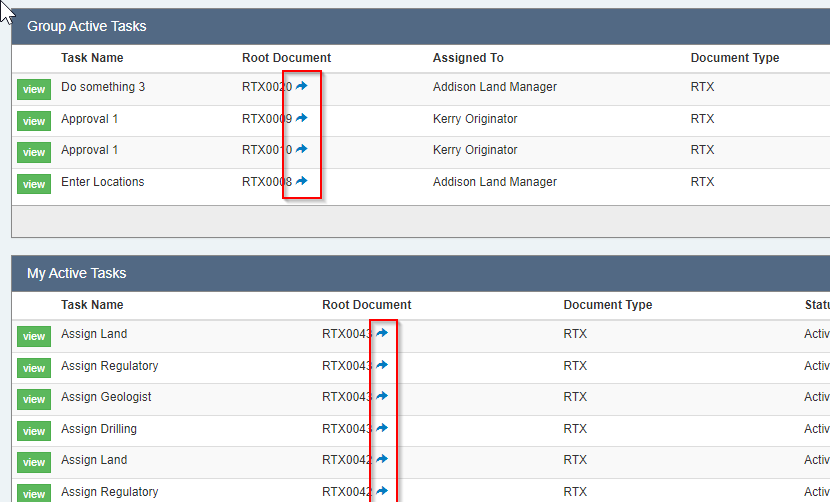
Similarly, there was no way to open the root document once you were viewing a task (either by clicking the “view” button next to the task in the dashboard, nor by clicking the link in the email), so we added those too.
Bugs
- Fixed an issue where an admin could create two columns whose names differed only by an underscore (i.e. AREA and AREA_) which would break OData reporting for those fields. #system #224490
- We fixed an issue where specifying an invalid view within a custom sub-tab (plugin) would incorrectly break/hide all tabs. We’re all for making errors obvious so that they get corrected, but this was a little over the top. #system #230872
- Fixed an issue where printing multiple forms on an AFE could fail intermittently. #afe #233247
- Fixed an issue where newly added rows in a grid (using non-default column grouping) would only appear after saving. #system #233344
- For those of you dealing with monster print jobs (taking longer than 30 minutes to run), we’ve fixed the issue where, after waiting all that time, your download would fail. #afe #234123
- Fixed an issue where Execute wouldn’t reconnect/reload after a service outage (for example, after restarting the service). Nothing a click of the Refresh button wouldn’t solve, but this is nicer now. #system #234148
- Resolved an issue where linking an AFE to a WellEz job would sometimes fail with a validation error on “NumberValue”. #wellez #234423
- Fixed an issue where calculated fields that referred to deleted workflow tasks could cause other calculated fields to inexplicably fail too. #workflow #formula #234905