This update contains loads of exciting new features and fixes, but a few of our favourites are:
- Support for resetting workflow tasks and restarting parts of a workflow
- Improvements to the integration with OnDemand Well Operations (WellEz) for multi-job AFEs
- Credentials for 3rd party systems are now stored in our equivalent of Fort Knox
- Quorum Execute is now “Quorum Execute” or “Execute” for short
Notes
- For those of you managing the Execute application server, the service name in the Services Control Panel has changed from “Quorum Execute” to “Execute”
Schema Changes
- WORKFLOW_INSTANCE.ROOT_DOC_GUID for AFE Workflows is now that AFE’s DOCUMENT_ID rather than the CHAIN_GUID. #163281
- New columns (REQ_MANUAL_COMPLETE, REACT_ON_DPNDCY) on WORKFLOW_DEF_TASK to track reactivation configuration. #158350
- New column REACTIVATED on WORKFLOW_INSTANCE_TASK to track whether task was reactivated. #158350
Enhancements
-
New system for managing sensitive credentials in Execute and avoiding the need to embed those credentials in plugin files.
#system
#security
#157817
In this update, we have made some HUGE improvements to how we store credentials for 3rd party systems (required for integrations).
What needed to change
Previously, some credentials were stored in the Execute database, while others were embedded in plugins and configuration files.
- Credentials in the database were suboptimal for several reasons:
- Users with read access to the database could potentially retrieve integration credentials
- When copying from PROD to TEST you could inadvertently end up with a TEST environment that was integrating with PROD data
- Access to credentials in the plugins and configuration files were typically limited to the IT folks who manage those systems, but it’s still not a best practice to do things that way.
What’s New
With this update, we’ve added a new credential storage mechanism.
- For those of you with on-prem Execute environments, this is an encrypted file called
credentials.binin your service’s config folder. This file is encrypted using the Windows Data Protection API and unusable for any user other than the user running the Execute service. (NOTE: this means that changing the user that runs the Execute service will render all credentials stored in this file unusable!) - For those of you with Quorum-hosted Execute environments, these credentials are stored securely in an Azure Key Vault.
All external credentials managed from within the Execute UI (Quorum OnDemand Well Operations (WellEz), Peloton, Enersight, and the Integration Agent) are automatically written to the new encrypted credential mechanism.
Relevant plugins and config file now support a sensitive information placeholder element which will refer to credentials stored in the credential store.
What happens on upgrade?
On upgrade, any database-stored credentials (such as WellEz, Peloton, Enersight, and the Integration Agent) will be automatically migrated to the secure credential store. Note that this will come with a change in behaviour as these credentials will no longer copy between Execute environments when you copy the database. While different, we strongly feel this is a much safer behaviour.
Any existing plugins/config files with embedded credentials will be left as-is. If desired, the process of migrating a secret from these files to the credential store is described below.
How do I add protection for credentials in my config and plugin files?
Many plugins (such as synchronizations to external systems) contain sensitive information like database connection strings.
<actual_cost_database>Data Source=SQL_Server;Initial Catalog=SQL_Server;Integrated Security=False;User ID=accounting;Password=hunter2;MultipleActiveResultSets=True</actual_cost_database>We can replace the password in the connection string with a placeholder label (prefixed with
@@@).<actual_cost_database>Data Source=SQL_Server;Initial Catalog=SQL_Server;Integrated Security=False;User ID=accounting;Password=@@@ACCOUNTING_PASSWORD;MultipleActiveResultSets=True</actual_cost_database>Then, an administrator with the
Edit External Credentialsadmin privilege can navigate toTools > Configuration > External Credentialsand set the value for that placeholder.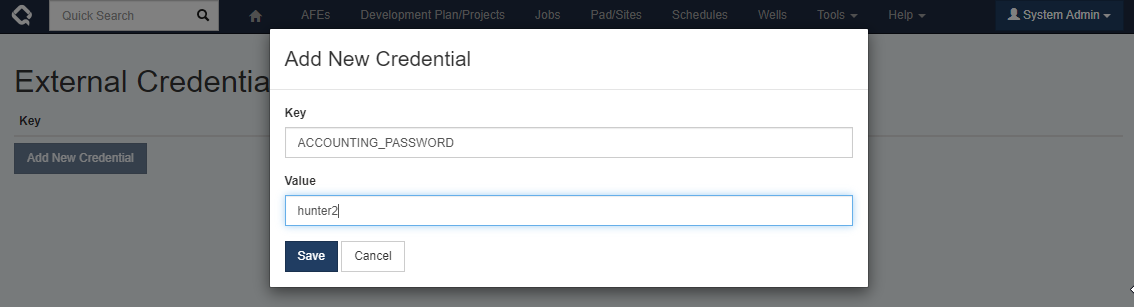
Now, when Execute tries to connect to the accounting database it will evaluate the connection string and replace the placeholder
@@@ACCOUNTING_PASSWORDwith the password we defined in the External Credentials screen.Note that for security purposes the password, once added, can never be read from the Execute UI. A best practice is to track integration passwords in a separate secure password management application so that they are available if needed in the future.
- Credentials in the database were suboptimal for several reasons:
-
Authorized users can now reset/reactivate workflow tasks, causing parts of the workflow to be re-run.
#workflow
#158680
The new advanced task-based workflow module in Execute is great and allows you to tightly control the collection of information on your Wells, Sites, Jobs, AFEs, etc.
Up until now, the workflow always marched forward. Once a task was complete, it would stay complete. There was no way to reactivate part of the workflow and force those tasks to be re-run.
<announcer_voice>Until today. . .</announcer_voice>
In this update, we’ve added phase 1 of a new workflow reset feature that allows a task owner or an administrator with the
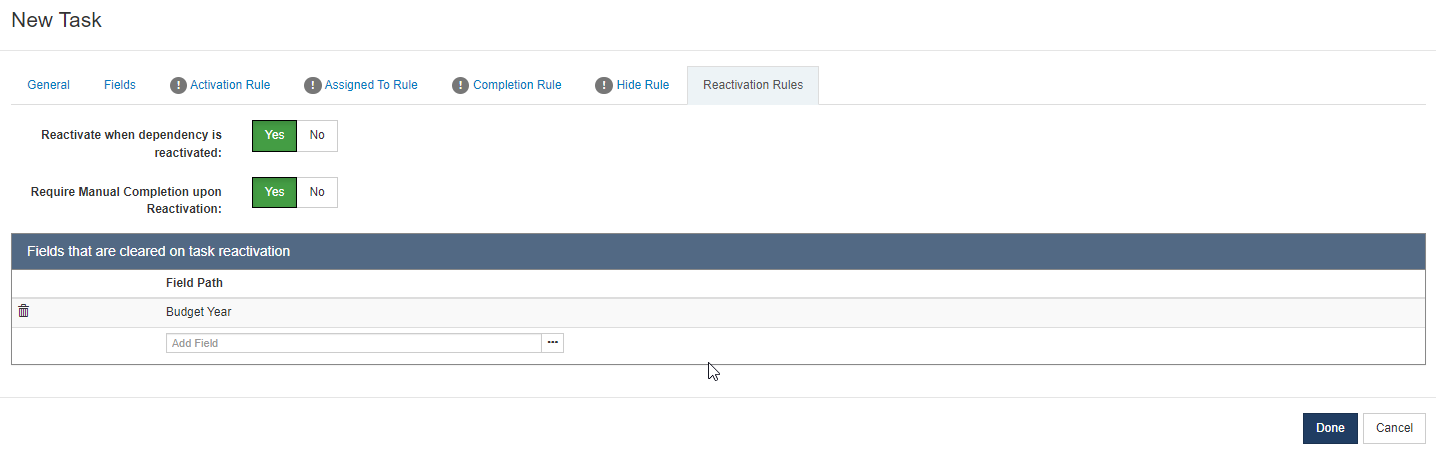
Can Reactivate Workflow Taskadmin privilege to reactive a task. As part of the workflow definition, administrators can now configure what happens when a task is reactivated, such as:- Does reactivating a task clear any data (forcing the user to re-enter those fields)?
- Does reactivating a task require the user to manually review/complete the task?
- If a parent task is reactivated, should the child/dependent task also be reactivated?
As mentioned, this is only the beginning.
In this update, task reactivation is a manual process.
Over the coming months, the plan is to introduce an automated aspect to this so that you can build rules like “If the location changes, automatically reset big chunks of the workflow.”
As part of this change, we have also cleaned up the behaviour of the “Manual Completion Behaviour”.
- If a task marked as “Require Manual Completion” has a Completion Rule, that completion rule must be satisfied before the task can be completed.
- If a task is not marked as “Require Manual Completion”, the task must have a Completion Rule to be completed. There is no option for a user to manually complete the task in this case. This is a change from the previous version where the software would incorrectly show a Complete button to the user.
- Tasks where “Require Manual Completion” = yes will show a “Save” and a “Save & Complete” button
- Tasks where “Require Manual Completion” = no will show a “Save” only
- Now that Execute is part of the Quorum family, we thought it was a good time to tweak things a bit. The product formerly known as “Quorum Execute” is now “Quorum Execute” or “Execute” for short. The application icons, logos, and branding have been updated accordingly. #system #security #159350
- To help keep things tidy, we’ve added an option to remove schedule activities that are no longer in your Enersight import dataset. #opsched #enersight #161131
- If you use OnDemand Well Operations (WellEz) and have AFEs that contain costs that apply to multiple jobs (such as a D&C AFE), we have good news! We’ve added support for pushing multi-job AFEs into WellEz. #well delivery #wellez #162398
- Workflows created against AFEs are now AFE-version specific and will reset when revisions/supplements are made. #workflow #afe #163281
- Adjusted browser caching from 24 hours to 15 minutes to avoid issues that pop up after upgrading Execute versions. #system #165822
- Support m-files:// links to the M-Files document management system #system #166537
- We’ve made the user experience a bit more consistent by ensuring that primary document types (AFE, WELL, RTx, SITE and PROJECT) always have vertical tabs. #system #172292
- We’ve cleaned up the interface a bit by hiding automatic Wells/Sites/Jobs tabs on Sites, Wells, Projects, etc. if those documents are not being used (i.e. There is not much point in showing an empty Wells tab on a Project if you aren’t using Execute’s Wells module). #system #172936
- After rolling out Document Validation Rules and Custom Field Permissions, we fully intended to allow you to create those rules on any record in the system. Unfortunately, overzealous validation shut that down when you tried to actually do that. We have “adjusted” that validation so that you may now add, for example, Document Validation rules to your Partners, AFE Types, etc. #system #174942
-
Added new Table*Filtered functions which allow extracting Min/Max/Count of a subset of the rows in a table.
#system
#175760
We’ve added some new functions to provide more options when building calculated fields against a subset of the data in a table.
- TableMaxDateFiltered - return the maximum date from a filtered subset of the rows in a table
- TableMinDateFiltered - return the minimum date from a filtered subset of the rows in a table
- TableMaxFiltered - return the maximum number from a filtered subset of the rows in a table
- TableMinFiltered - return the minimum number from a filtered subset of the rows in a table
- TableSumFiltered - return the sum of a numeric field on a filtered subset of the rows in a table
- TableCountFiltered - return the count of a filtered subset of the rows in a table
All of the above work like their non-filtered counterparts, but introduce two new parameters:
filterPath- is the path to a field on the table row that we are going to use to filter the rows.filterValue- is a text value that we are going to compare to the value of the field infilterPath. The function will only process/include rows where thefilterValueis a match to thefilterPathvalue.
For example:
If I have a custom table for tracking Contract details (
CUSTOM/CONTRACTS) and I wanted to return the most recent contract date (CUSTOM/CONTRACTS/CONTRACT_DATE) for any “Land”-type contract (CUSTOM/CONTRACTS/CONTRACT_TYPE= “Land”), I would use a formula like this:TableMaxDateFiltered("CUSTOM/CONTRACTS","CONTRACT_DATE","CONTRACT_TYPE","Land")(note: the fields above must be enclosed in quotes and not square brackets in this case.)
- We have also included sample configuration for deploying sub-tabs which may be helpful in simplifying layout for those of you with huge numbers of fields. #system #172292
-
Execute previously relied on the older NTLM protocol for on-prem single sign-on. In this release we’ve also enabled Kerberos support. If this causes problems on your environment either NTLM or Kerberos can be disabled.
#system
#security
#175304
We will enable both types of authentication by default. They can be turned off by adding one of the following to the
<castle>container inuser.config.
Bugs
- Fixed incorrect error message when trying to use a new build of the Database Tool to copy an older (pre-21.1.212) Execute database. #system #166602
- Fixed issue where unscheduled activities in OpSched would cause a Null Reference Exception when updating Project timing. #opsched #171827
- Removed the old Aucerna blog widget that was throwing exceptions in the system log. #system #175280